概要
前回作成したプロキシサーバに対して、SSL可視化用の設定を追加する。
・HTTPSのバス部分までProxyログとして取得
・ブラックリスト/ホワイトリストによるHTTPSのURL制御
・一部のURLはSSLを透過させる
前提
プロキシ動作が squid(ver3.5)を使用している環境
簡易構成
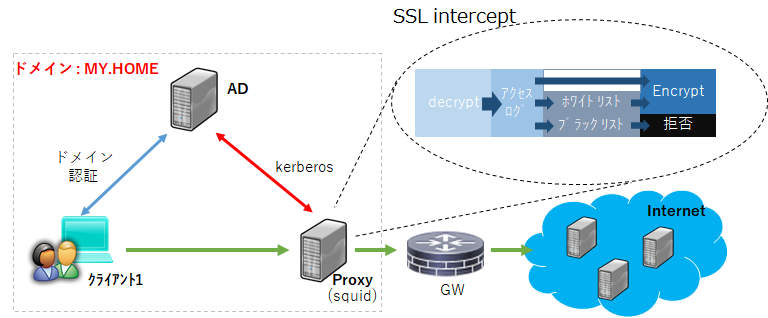
ざっくりしたフロー図(イメージ)
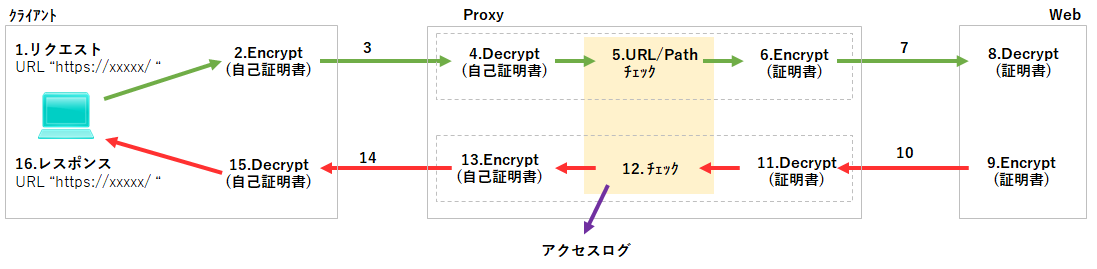
今後の課題と検討
bump . peekなどの動作が正確に分からないので確認が必要
ブラックリストによる遮断は動いていそうだけどよくわからない。
証明書関連のログで取得できる項目を確認し、取得する項目として追加する必要があるのか検討する
Ver3.5よりVer4.xのほうが設定オプションが多いのでVer4.xで再構築するほうが良いのか?
■Ver3.5のログフォーマット ※SSL-related format codesを参照
http://www.squid-cache.org/Versions/v3/3.5/cfgman/logformat.html
■Ver4のログフォーマット ※SSL-related format codesを参照
http://www.squid-cache.org/Versions/v4/cfgman/logformat.html
環境概要
Domain = my.home
サブネット= 172.16.100.0/24
プロキシサーバー
OS = CentOS 7.5
squid 3.5.20
IP = 172.16.100.190
HOSTNAME = squid2.my.home
Kerberosコンピューター名= squid2
AD(Windows Server 2016) ※DNS,NTPサーバも兼ねる
IP = 172.16.100.100
HOSTNAME = ad.my.home
クライアント(windows 10 )
ドメインユーザ = test01
IP = 172.16.100.41
手順
クライアント~Proxt間で使用する自己証明書作成
証明書保存用ディレクトリ作成
[root@proxy2 ~]# mkdir /etc/squid/cert
[root@proxy2 ~]# chown squid:squid /etc/squid/cert
[root@proxy2 ~]# chmod 700 /etc/squid/cert
[root@proxy2 ~]# ls -l /etc/squid/cert
合計 0
[root@proxy2 ~]# ls -l /etc/squid/
~省略~
drwx------ 2 squid squid 6 4月 11 21:43 cert
~省略~
[root@proxy2 ~]# cd /etc/squid/cert
[root@proxy2 cert]#
自己署名ルート証明書の作成
■設定値
- ファイル名:privateCA.pem ※秘密鍵と同一のファイル名で作成
- subject: OU=priveteCA , C=JP , CN=private
※住所まで細かく設定を入れると移転する際に作り直す必要がるので不要でいいかも。
※会社名を入れる場合は、英語表記が無難かも。
- 期間 :365日 ※ローカル証明書なので 任意の期間で設定が可能 (day:3650/10年とか)
[root@proxy2 cert]# openssl req -new -newkey rsa:2048 -sha256 -days 365 -nodes -x509 -extensions v3_ca -subj "/OU=privateCA/C=JP/CN=private" -keyout privateCA.pem -out privateCA.pem
Generating a 2048 bit RSA private key
..................................+++
....................................................................................................................................+++
writing new private key to 'privateCA.pem'
-----
[root@proxy2 cert]# ls -l
合計 4
-rw-r--r-- 1 root root 2888 4月 11 21:47 privateCA.pem
[root@proxy2 cert]#
[root@proxy2 cert]# openssl x509 -in privateCA.pem -outform DER -out privateCA.der
[root@proxy2 cert]# ls -l
合計 8
-rw-r--r-- 1 root root 829 4月 11 22:05 privateCA.der
-rw-r--r-- 1 root root 2888 4月 11 21:47 privateCA.pem
[root@proxy2 cert]#HTTPS用にSquid構成を行う
squid.confの修正
ログフォーマットは、"bump_mode=%ssl::bump_mode" , "sni=%ssl::>sni" を追加して情報取得するように修正する。
[root@proxy2 ~]# vi /etc/squid/squid.conf
--追加--
#SSL setup
sslproxy_options NO_SSLv2,NO_SSLv3,NO_TLSv1,SINGLE_DH_USE
sslcrtd_program /usr/lib64/squid/ssl_crtd -s /var/lib/squid/ssl_db -M 4MB
sslcrtd_children 5
#SSL fileter
acl https_whitelist ssl::server_name_regex -i "/etc/squid/list/whitelist_001.txt"
acl https_blacklist ssl::server_name_regex -i "/etc/squid/list/blacklist_001.txt"
acl step1 at_step SslBump1
acl step2 at_step SslBump2
acl step3 at_step SslBump3
ssl_bump peek step1 all
ssl_bump peek step2 https_whitelist
ssl_bump splice step3 https_whitelist
ssl_bump terminate step2 https_blacklist
ssl_bump bump all
# Deny CONNECT to other than secure SSL ports
http_access deny CONNECT !SSL_ports
#logformat
logformat customlog "time=%{%Y/%m/%d %H:%M:%S}tl","bump_mode=%ssl::bump_mode","sni=%ssl::>sni","un=%un","credentials=%credentials","host=%>la","src_ip=%>a","src_port=%>p","dest_ip=%<a","dest_port=%<p","url=%ru","status=%>Hs","http_method=%rm","referer=%{Referer}>h","user=%ui","duration=%tr","dt=%dt","uri_path=%>rp","byte_in=%<st","byte_out=%>st","http_user_agent=%{User-Agent}>h","content_type=%mt","action=%Ss","product=squid"
access_log /var/log/squid/access.log customlog
※HTTP://xxxxx/ はブロックされないので HTTP用のブラックリスト作成は必要
ブラックリスト,ホワイトリスト作成
ブラックリスト:https://5ch.net -> 5ch\.net
ホワイトリスト:https://www.yahoo.co.jp -> www\.yahoo\.co\.jp
記載は正規表現が可能で特殊文字はエスケープする必要がある。
[root@proxy2 ~]# mkdir /etc/squid/list
[root@proxy2 ~]# cd /etc/squid/list
[root@proxy2 list]# vi blacklist_001.txt
5ch\.net
[root@proxy2 list]# vi whitelist_001.txt
www\.yahoo\.co\.jp
[root@proxy2 list]#
設定反映
[root@proxy2 ~]# squid -k parse
[root@proxy2 ~]# squid -k check
[root@proxy2 ~]# squid -k reconfigure
クライアントに自己証明書インストール
作成した自己署名ルート証明書をクライアントPC内に証明書ファイル(privateCA.der)の保存する。
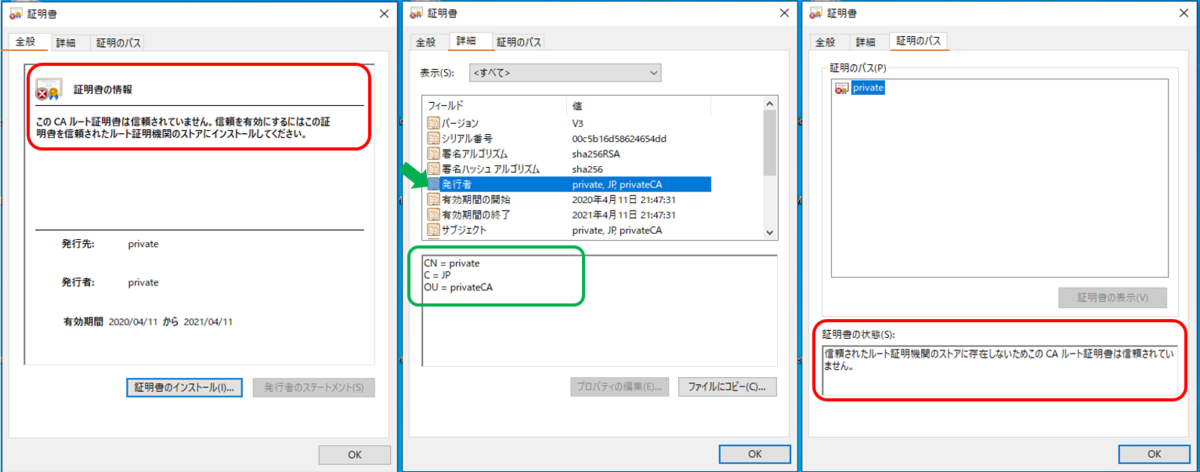
保存した証明書の内容確認
"全般"タブや"証明書のパス"タブから現状の信頼されない証明書として認識していること、"詳細"タブから設定したsubject内容や有効期限などが分かる。
証明書のインポートを実施
1.ファイルを右クリックして証明書のインストールを選択する。
2.保存場所は必要に応じて選択し「次へ」をクリックする
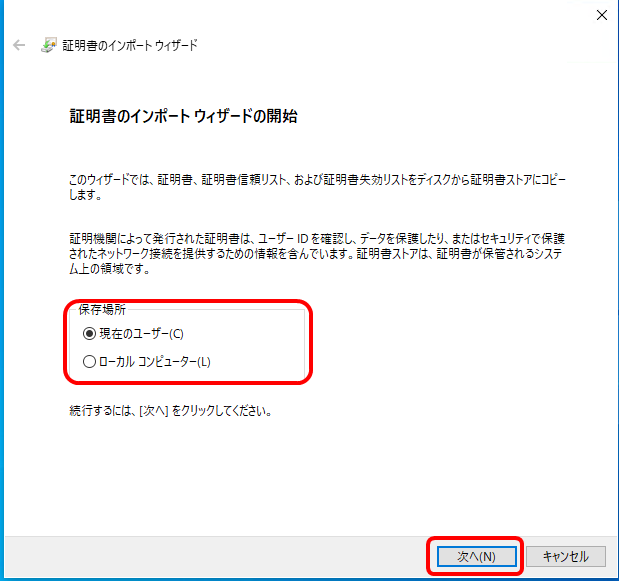
3.「証明書をすべて次のストアに配置する」を選択し、参照から”信頼されたルート証明機関”を選択する
証明書ストアへ”信頼されたルート証明機関”と表示されたことを確認し、「次へ」をクリックする。
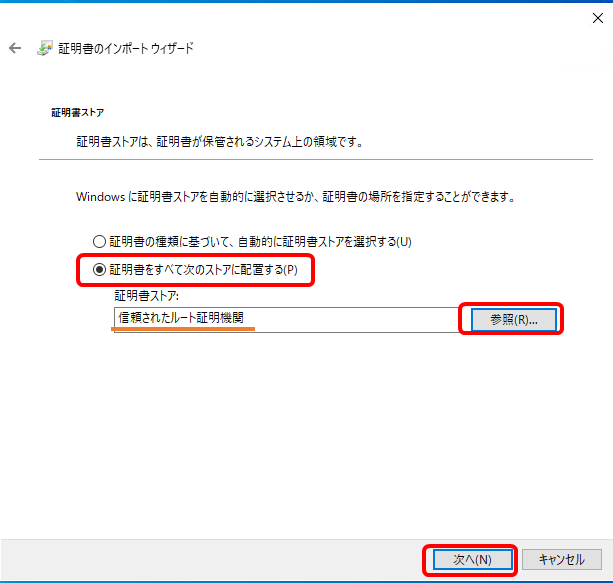
4.「完了」をクリックする。
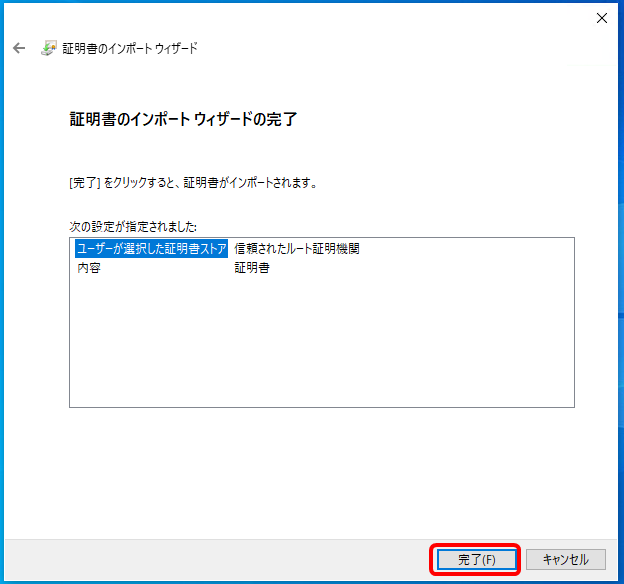
5.セキュリティ警告は、インストールを実施するため「はい」をクリックする。
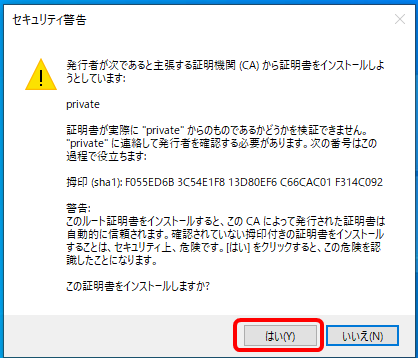
6.正常にインポートが終わることを確認し、「OK」をクリックする。
7.以降は、インポートした証明書確認を実施する手順となる。
IEやChromからインターネットオプション設定を開き、コンテンツタブの「証明書」をクリックする。
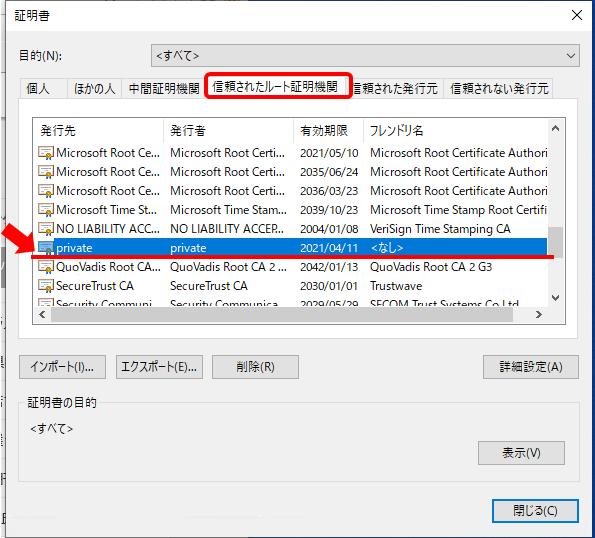
8.信頼されたルート証明機関タブを選択して、証明書リスト内にインポートした証明書があることを確認する。
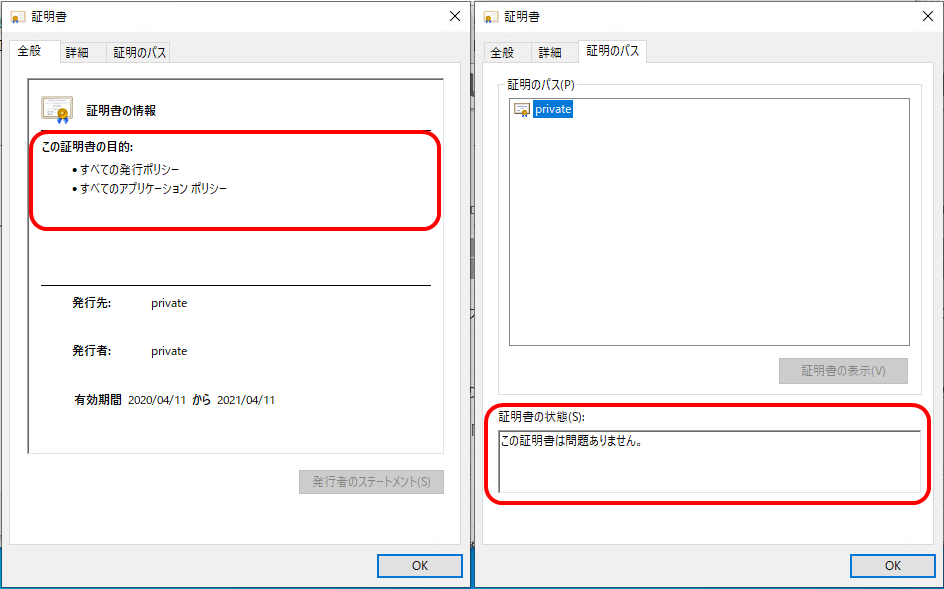
9.上記手順で該当証明書クリックし、証明書が問題ないことを確認する。
(信頼されない証明書ではなくなることが分かる)
動作確認①
ブラウザからアクセス
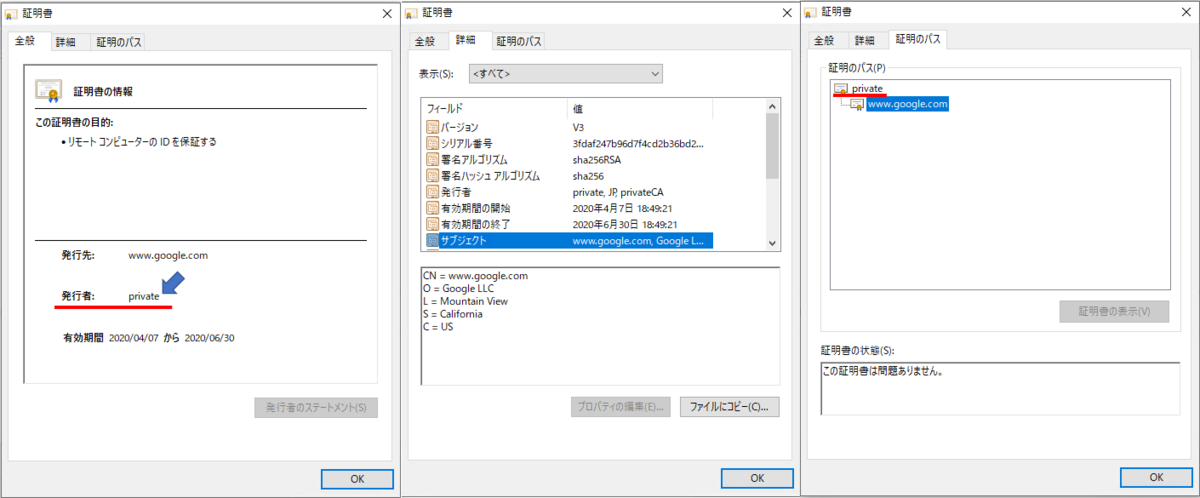
証明書の内容を確認
→ルート証明書が作成して自己証明書であることがわかる。
アクセスログ①
"time=2020/05/03 00:26:18","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=56434","dest_ip=-","dest_port=-","url=www.google.com:443","status=407","http_method=CONNECT","referer=-","user=-","duration=0","dt=-","uri_path=-","byte_in=4091","byte_out=224","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:26:18","bump_mode=peek","sni=www.google.com","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=56434","dest_ip=172.217.161.68","dest_port=443","url=www.google.com:443","status=200","http_method=CONNECT","referer=-","user=-","duration=142","dt=-","uri_path=-","byte_in=0","byte_out=2445","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=-","action=TAG_NONE","product=squid"アクセスログ② Googleニュースにアクセスした場合
無事にURIのPATH部分もログに記録されていることが確認できる。
"time=2020/05/03 00:34:03","bump_mode=bump","sni=news.google.com","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=56575","dest_ip=216.58.199.238","dest_port=443","url=https://news.google.com/_/DotsSplashUi/data/batchexecute?","status=0","http_method=POST","referer=https://news.google.com/","user=-","duration=72","dt=-","uri_path=/_/DotsSplashUi/data/batchexecute?rpcids=xZTw2c&f.sid=4184459597273559624&bl=boq_dotssplashserver_20200424.09_p10&hl=ja&gl=JP&soc-app=140&soc-platform=1&soc-device=1&_reqid=202020&rt=c","byte_in=0","byte_out=2061","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=-","action=TCP_MISS_ABORTED","product=squid"
"time=2020/05/03 00:34:06","bump_mode=bump","sni=news.google.com","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=56578","dest_ip=216.58.199.238","dest_port=443","url=https://news.google.com/dssw.js?","status=200","http_method=GET","referer=https://news.google.com/","user=-","duration=128","dt=-","uri_path=/dssw.js?xhrRoot=/_/DotsSplashUi&mssRowKey=boq-dots.DotsSplashUi.ja.VMFVh7G8gdA.es5.O&buildLabel=boq_dotssplashserver_20200424.09_p10&initialJsPath=https://www.gstatic.com/_/mss/boq-dots/_/js/k%3Dboq-dots.DotsSplashUi.ja.VMFVh7G8gdA.es5.O/am%3DC3ADQAg/d%3D1/excm%3D_b,_tp,topstories/ed%3D1/dg%3D0/wt%3D2/ct%3Dzgms/rs%3DALs0n2MASC5dqTIgLClSW5T3GPZ68n0bcw/m%3D_b,_tp","byte_in=1151","byte_out=1364","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=application/javascript","action=TCP_MISS","product=squid"
動作確認② ホワイトリスト
ブラウザからアクセス
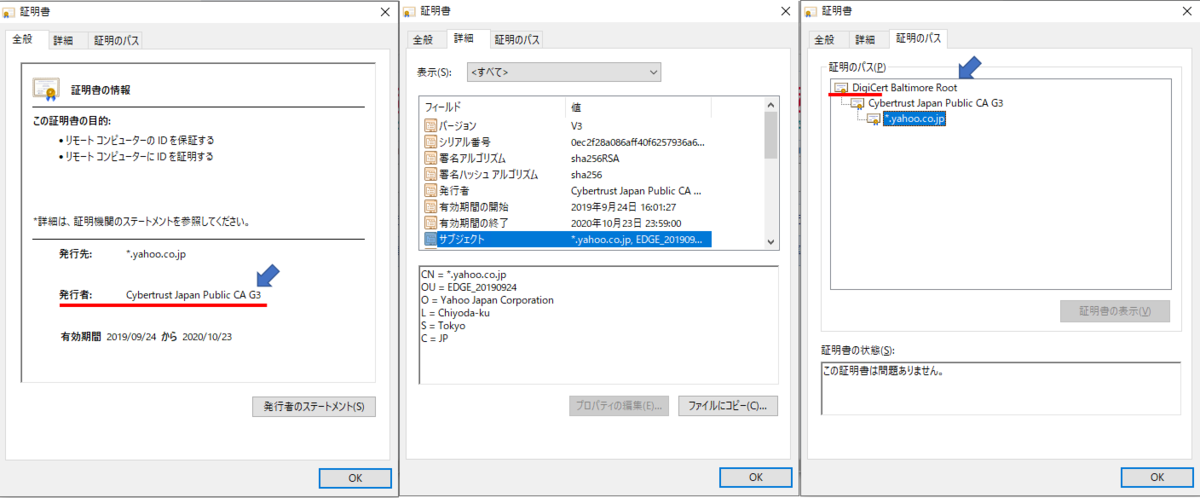
証明書の内容を確認
→ルート証明書が自己証明書では無いでことがわかる。
アクセスログ
"time=2020/05/03 00:41:06","bump_mode=peek","sni=www.yahoo.co.jp","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=56664","dest_ip=182.22.16.251","dest_port=443","url=www.yahoo.co.jp:443","status=200","http_method=CONNECT","referer=-","user=-","duration=136708","dt=54","uri_path=-","byte_in=67408","byte_out=2447","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=-","action=TCP_TUNNEL","product=squid"
"time=2020/05/03 00:42:52","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=56893","dest_ip=-","dest_port=-","url=www.yahoo.co.jp:443","status=407","http_method=CONNECT","referer=-","user=-","duration=5","dt=-","uri_path=-","byte_in=4095","byte_out=226","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:42:52","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=56897","dest_ip=-","dest_port=-","url=www.yahoo.co.jp:443","status=407","http_method=CONNECT","referer=-","user=-","duration=0","dt=-","uri_path=-","byte_in=4095","byte_out=226","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
動作確認③ ブラックリスト
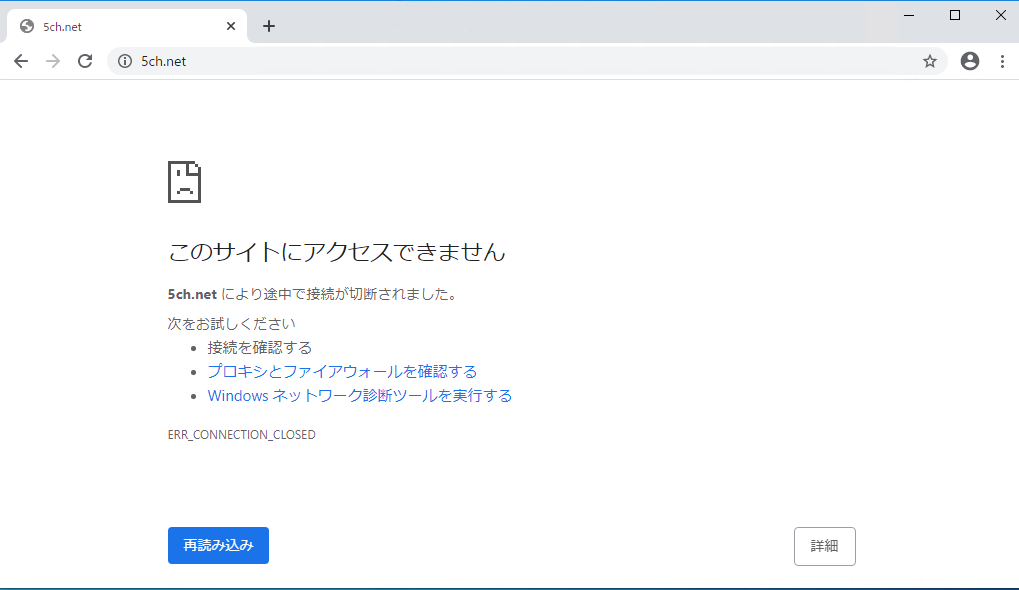
アクセスログ
"time=2020/05/03 00:49:22","bump_mode=peek","sni=5ch.net","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=57618","dest_ip=-","dest_port=-","url=5ch.net:443","status=200","http_method=CONNECT","referer=-","user=-","duration=73","dt=-","uri_path=-","byte_in=0","byte_out=2431","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=-","action=TAG_NONE","product=squid"
"time=2020/05/03 00:49:30","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57620","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=4","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:49:30","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57621","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=0","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:49:30","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57622","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=0","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:49:30","bump_mode=peek","sni=5ch.net","un=test01@MY.HOME","credentials=KK (null)\n","host=172.16.100.190","src_ip=172.16.100.41","src_port=57622","dest_ip=-","dest_port=-","url=5ch.net:443","status=200","http_method=CONNECT","referer=-","user=-","duration=61","dt=-","uri_path=-","byte_in=0","byte_out=2431","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=-","action=TAG_NONE","product=squid"
"time=2020/05/03 00:49:33","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57625","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=5","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:49:33","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57624","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=1","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
"time=2020/05/03 00:49:33","bump_mode=-","sni=-","un=-","credentials=-","host=172.16.100.190","src_ip=172.16.100.41","src_port=57626","dest_ip=-","dest_port=-","url=5ch.ne :443","status=407","http_method=CONNECT","referer=-","user=-","duration=0","dt=-","uri_path=-","byte_in=4063","byte_out=210","http_user_agent=Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.122 Safari/537.36","content_type=text/html","action=TCP_DENIED","product=squid"
参考URL
・Configuring a Squid Server to authenticate from Kerberos
https://wiki.squid-cache.org/ConfigExamples/Authenticate/Kerberos
