- 構成
- やりたいこと
- (参考)ZAP-CLIコマンドオプション
- (参考)ZAP-CLI(SCAN関連)コマンドオプション
- (参考)ZAP-CLI(Log/report関連)コマンドオプション
- Scanの実行結果
構成
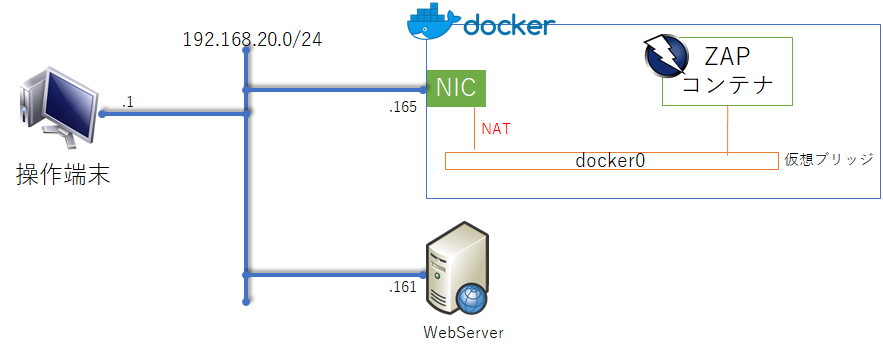
やりたいこと
zap-cli を使用して、zapbaselineみたいなScanを実施する
参考 https://github.com/Grunny/zap-cli
■実施概要
1.Docker起動
※ディレクトリ共有とし、そのDockerとの共有ディレクトリへreport出力とする。
※実施バージョン: weekly/OWASP ZAP D-2017-12-18
358 [main] INFO org.zaproxy.zap.GuiBootstrap - OWASP ZAP D-2017-12-18 started
2.zap-cliを使用したScanの実施
1.起動確認
2.Scan対象との接続性確認
3.Spiderの実施
4.active-scanの実施
3.report出力
1.結果出力(high以上:デフォルト値)
2.xmlでファイル出力
■Scan実施方法
#!/bin/sh
CONTAINER_ID=$(docker run -v $(pwd):/zap/wrk/:rw -u root -p 8080:8080 -i -d owasp/zap2docker-weekly zap.sh -daemon -host 0.0.0.0 -port 8080 -config api.disablekey=true -config api.addrs.addr.name=.* -config api.addrs.addr.regex=true)
#target
TARGET_URL=$1
#SCAN start
docker exec $CONTAINER_ID zap-cli -p 8080 status
docker exec $CONTAINER_ID zap-cli -p 8080 open-url $TARGET_URL
docker exec $CONTAINER_ID zap-cli -p 8080 spider $TARGET_URL
docker exec $CONTAINER_ID zap-cli -p 8080 active-scan -r $TARGET_URL
#Output
docker exec $CONTAINER_ID zap-cli -p 8080 alerts
docker exec $CONTAINER_ID zap-cli report -f xml -o /zap/wrk/testreport_$(date +%Y%m%d).xml
※CONTAINER_IDの取得で、参考にしたサイトの実施コマンドでも取得できるがコンテナが起動しなかった。
※レポート出力用ディレクトリもzapbaselineをもとにオプション指定を実施
(参考)ZAP-CLIコマンドオプション
■zap-cli オプション設定
zap@86562aa52fa1:/zap$ zap-cli --help
Usage: zap-cli [OPTIONS] COMMAND [ARGS]...
ZAP CLI v0.9.0 - A simple commandline tool for OWASP ZAP.
Options:
--boring Remove color from console output.
-v, --verbose Add more verbose debugging output.
--zap-path TEXT Path to the ZAP daemon. Defaults to /zap or the value of
the environment variable ZAP_PATH.
-p, --port INTEGER Port of the ZAP proxy. Defaults to 8090 or the value of
the environment variable ZAP_PORT.
--zap-url TEXT The URL of the ZAP proxy. Defaults to http://127.0.0.1
or the value of the environment variable ZAP_URL.
--api-key TEXT The API key for using the ZAP API if required. Defaults
to the value of the environment variable ZAP_API_KEY.
--help Show this message and exit.
Commands:
active-scan Run an Active Scan.
ajax-spider Run the AJAX Spider against a URL.
alerts Show alerts at the given alert level.
context Manage contexts for the current session.
exclude Exclude a pattern from all scanners.
open-url Open a URL using the ZAP proxy.
policies Enable or list a set of policies.
quick-scan Run a quick scan.
report Generate XML or HTML report.
scanners Enable, disable, or list a set of scanners.
scripts Manage scripts.
session Manage sessions.
shutdown Shutdown the ZAP daemon.
spider Run the spider against a URL.
start Start the ZAP daemon.
status Check if ZAP is running.
zap@86562aa52fa1:/zap$
(参考)ZAP-CLI(SCAN関連)コマンドオプション
■zap-cli active-scan オプション設定
zap@86562aa52fa1:/zap$ zap-cli active-scan --help
Usage: zap-cli active-scan [OPTIONS] URL
Run an Active Scan against a URL.
The URL to be scanned must be in ZAP's site tree, i.e. it should have
already been opened using the open-url command or found by running the
spider command.
Options:
-s, --scanners TEXT Comma separated list of scanner IDs and/or groups
to use in the scan. Use the scanners subcommand to
get a list of IDs. Available groups are: all, sqli,
xss_persistent, xss_reflected, xss.
-r, --recursive Make scan recursive.
-c, --context-name TEXT Context to use if provided.
-u, --user-name TEXT Run scan as this user if provided. If this option
is used, the context parameter must also be
provided.
--help Show this message and exit.
zap@86562aa52fa1:/zap$
■zap-cli spider オプション設定
zap@86562aa52fa1:/zap$ zap-cli spider --help
Usage: zap-cli spider [OPTIONS] URL
Run the spider against a URL.
Options:
-c, --context-name TEXT Context to use if provided.
-u, --user-name TEXT Run scan as this user if provided. If this option
is used, the context parameter must also be
provided.
--help Show this message and exit.
zap@86562aa52fa1:/zap$
(参考)ZAP-CLI(Log/report関連)コマンドオプション
■zap-cli alerts オプション設定
zap@86562aa52fa1:/zap$ zap-cli alerts --help
Usage: zap-cli alerts [OPTIONS]
Show alerts at the given alert level.
Options:
-l, --alert-level [High|Medium|Informational|Low]
Minimum alert level to include in report
(default: High).
-f, --output-format [table|json]
Output format to print the alerts.
--exit-code BOOLEAN Whether to set the exit code to the number
of alerts (default: True).
--help Show this message and exit.
zap@86562aa52fa1:/zap$
■zap-cli report オプション設定
zap@86562aa52fa1:/zap$ zap-cli report --help
Usage: zap-cli report [OPTIONS]
Generate XML or HTML report.
Options:
-o, --output TEXT Output file for report.
-f, --output-format [xml|html] Report format.
--help Show this message and exit.
zap@86562aa52fa1:/zap$
Scanの実行結果
zap-cli確認
※test.sh:上記のシェルスクリプトのファイル名
[root@sv01 ~]# ./test.sh http://192.168.20.161 ※ここでスキャン対象を入力
[INFO] ZAP is running #コマンドの実施ログ
[INFO] Accessing URL http://192.168.20.161 #コマンドの実施ログ
[INFO] Running spider... #コマンドの実施ログ
[INFO] Running an active scan... #コマンドの実施ログ
[INFO] Issues found: 22
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Alert | Risk | CWE ID | URL |
+==============================+========+==========+===================================================================================================+
| Source Code Disclosure - SVN | High | 541 | http://192.168.20.161/search/feed |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/1 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/1 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/1?replytocom=1 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/1?replytocom=1 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/author |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/author/user |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/category |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/category/%e6%9c%aa%e5%88%86%e9%a1%9e |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/date |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/date/2017 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/archives/date/2017/10 |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/comments |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/search |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/search/feed |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/sitemap.xml |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/wp-login.php?action=lostpassword |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/wp-login.php |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/wp-login.php?action=lostpassword |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/wp-login.php |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
| Anti CSRF Tokens Scanner | High | 352 | http://192.168.20.161/wp-login.php?reauth=1&redirect_to=http%3A%2F%2F192.168.20.161%2Fwp-admin%2F |
+------------------------------+--------+----------+---------------------------------------------------------------------------------------------------+
[INFO] Report saved to "/zap/wrk/testreport_20171220.xml"
[root@sv01 ~]# ls -al testreport_20171220.xml
-rw-r--r-- 1 root root 58746 12月 20 22:53 testreport_20171220.xml
[root@sv01 ~]#
Scanが無事に完了し、report取得ができた。